Intro
Microsoft’s Entra application gallery is a collection of software as a service (SaaS) applications preintegrated with Microsoft Entra ID. Users can search for and deploy apps that are tested and certified by Microsoft. Both Premium and Standard users can integrate with Domo for Single Sign-On (SSO). To set up SSO, you must have a Domo Admin system role or a custom role with the Manage All Company Settings grant enabled. Learn more about grants and custom roles. This article describes how to implement SSO with Entra ID.Implement SSO with Entra ID
- Sign in to the Microsoft Entra admin center, at least as a Cloud Application Administrator.
- Go to Identity > Applications > Enterprise applications > Domo > Single sign-on.
- On the Select a single sign-on method page, select SAML.
-
On the Set up single sign-on with SAML page, select Edit.

- In a separate browser tab, log into Domo as an Admin user and navigate to More > Admin to view the Admin Settings.
-
Under Authentication, select SAML (SSO).
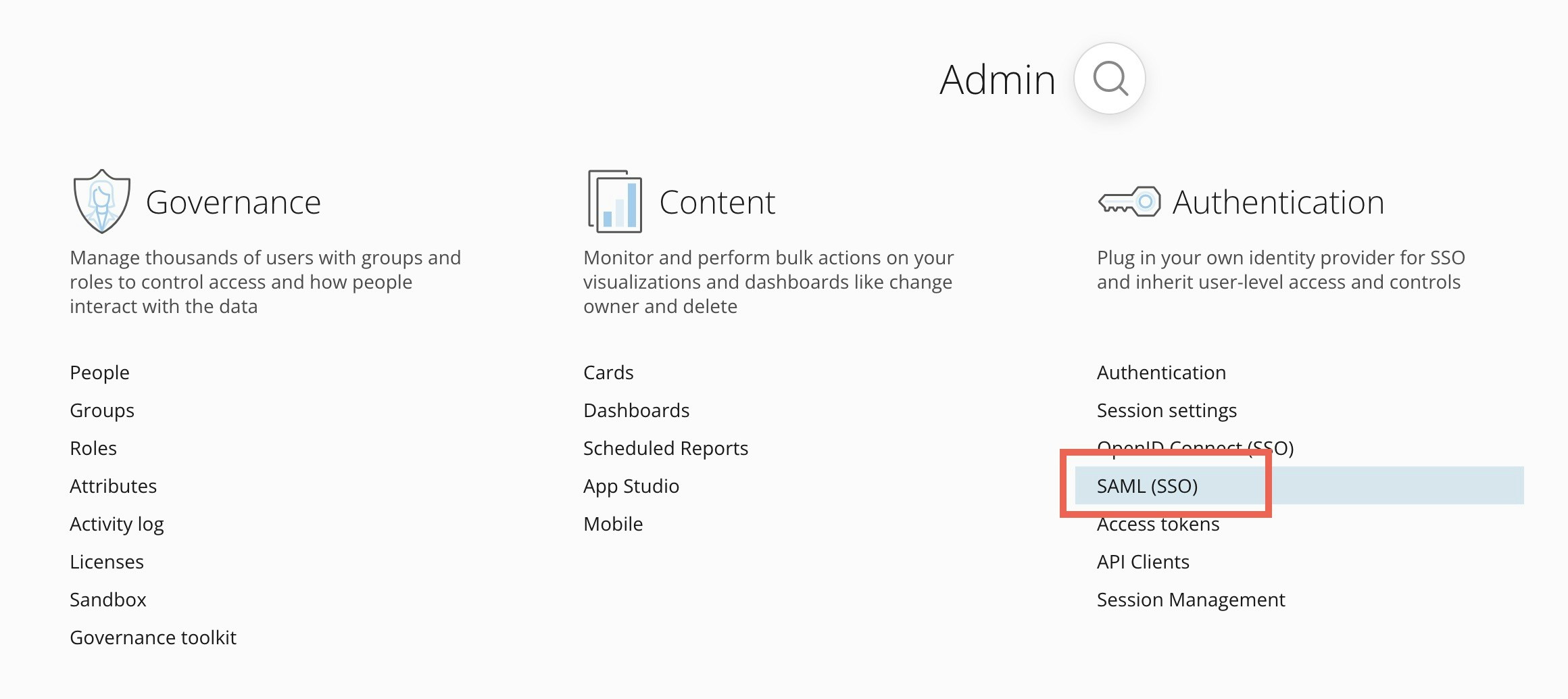
-
On the SAML (SSO) page, select Start Setup > Manual setup.

-
Under Information your IdP may need, copy the URL in the SAML Assertion Endpoint URL field up to “.com” (the highlighted portion in the image below). This will be used for both the Entra Sign On URL and Identifier (Entity ID) fields.
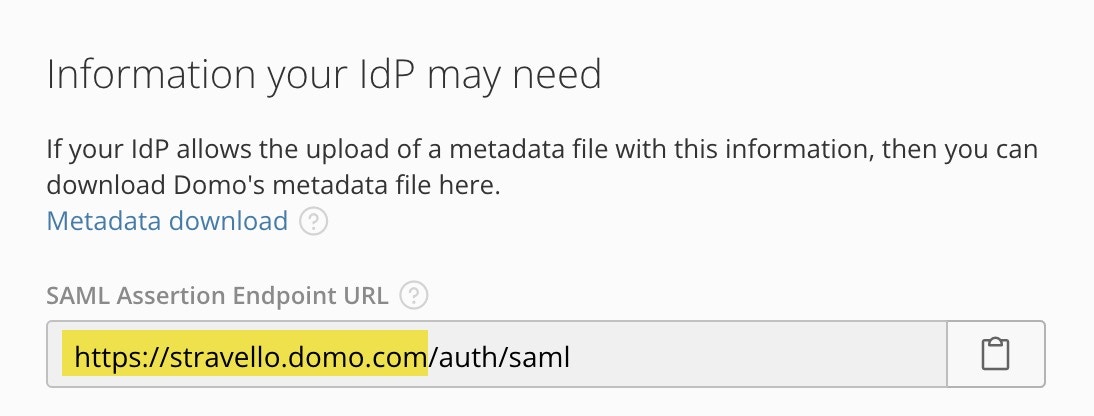
- Return to the Entra browser tab.
-
In the Basic SAML Configuration section, enter the values for the following fields:
- In the Sign on URL text box, paste the URL you copied from Domo.
- In the Identifier (Entity ID) text box, paste the same URL you copied from Domo.
-
Copy the URL from the Login URL field. (Note that this URL is the same as the one in the Logout URL.)
Note: You may ignore the Microsoft Entra ID Identifier URL as this is not used.

- Return to Domo.
-
Under Information from your IdP, paste the URL from the previous step into the Identity provider endpoint URL field.
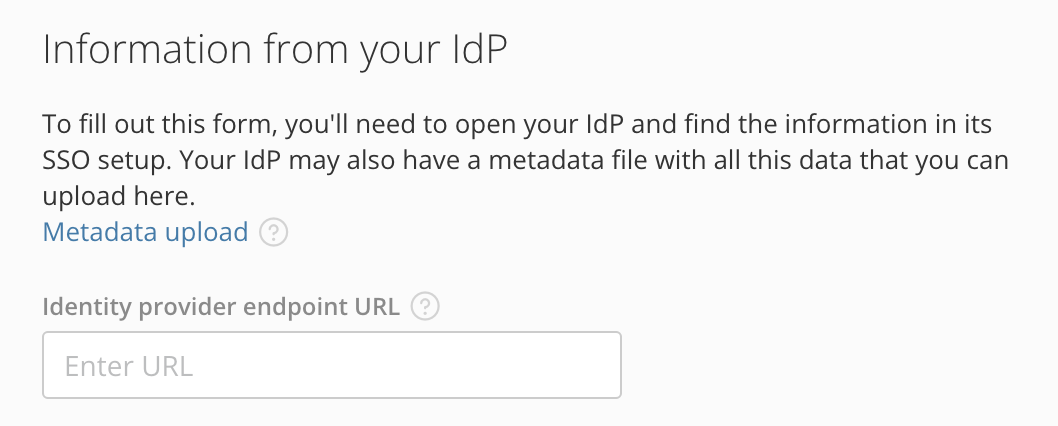
-
In the Entity ID field, paste the value from step 8 (the highlighted portion).
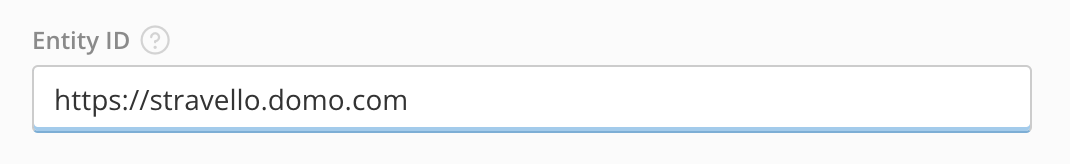
- Return to Entra.
-
On the Set up single sign-on with SAML page, in the SAML Signing Certificate section, find Certificate (Base64) and select Download to download the certificate and save it to your computer.

- Return to Domo.
-
Under Information from your IdP, select
 Upload (up arrow icon) in the Upload x.509 certificate to authenticate request field and add the Base64 certificate you just downloaded.
Upload (up arrow icon) in the Upload x.509 certificate to authenticate request field and add the Base64 certificate you just downloaded.
-
(Optional) Check the boxes under Advanced settings to configure them. A few are defined below:
- Only invited people can access Domo — This prevents Entra ID users from logging into Domo through SSO until they are invited to Domo. (By default, when SSO is enabled in Domo, any user in your Entra ID directory can log into Domo.)
-
Import guests from identity provider — This copies your groups from Entra to Domo. Note: Entra doesn’t currently support groups that represent company departments, so Domo doesn’t recommend enabling this option.
Note: Entra sometimes imports the Group ID rather than the name of the group. You can edit the group name in the Domo Admin Settings under Governance > Groups.
- At the top of the Single Sign-On (SSO) page, toggle the switch labeled Enable SSO.
- Return to Entra.
- Before continuing, you must configure your Domo SAML token attributes. If you don’t, then the Entra ID default settings will be used and usernames within Domo will be overwritten with email addresses.
-
To configure your SAML token attributes, select ATTRIBUTES.

-
Configure the user information that is sent to Domo.
Domo accepts the following attribute names, and Entra allows you to assign values. When defining attributes passed back to Domo, use the attribute names listed in the table below. The
emailattribute is required; all others are optional.
Attribute | Description |
|---|---|
name | The full name of the user |
name.personal | The user’s first name |
name.family | The user’s last name |
email* | The email address of the user |
email.secondary | A secondary email address for the user |
title | The job title of the user |
user.phone | The primary phone number of the user, usually a mobile phone number |
desk.phone | The number for the user’s desk phone |
group | The group that the user belongs to, usually a department name |
role | The user’s role in the company |
employee. id | The user’s employee ID |
hire.date | The user’s hire date |
title | The user’s job title |
department | The user’s department in the company |
location | The company location for the user |
locale | The user’s locale, which determines settings such as number formats, measurements, etc. |
timezone | The user’s time zone |
name and email attributes within Entra ID.
-
Below are the default Entra ID attributes. Delete all rows (except for the first row, which cannot be removed). To delete a row, hover over it and select the Delete (x icon). Delete rows with names ending in
claims/givenname,claims/surname,claims/emailaddress,andclaims/name.If you make a mistake, Entra allows you to “reset to default” and start over. After you delete the unnecessary rows, your list should look like the list below. It contains only one row with a name ending in
claims/nameidentifier.
-
Add two new rows for
nameandemailwith values that Domo expects.-
To add a row for
name,do the following:- Select add user attribute. The Add User Attribute modal displays.
-
Enter
namein the ATTRIBUTE NAME field. -
Select user.displayname in the ATTRIBUTE VALUE dropdown.

- Select the checkmark at the bottom right of the modal.
Note: Display Name is the default field that contains the user’s full name. If you customize this field or do not use it, you may need to contact the Entra team for help in identifying which field to use to get the user’s full name. -
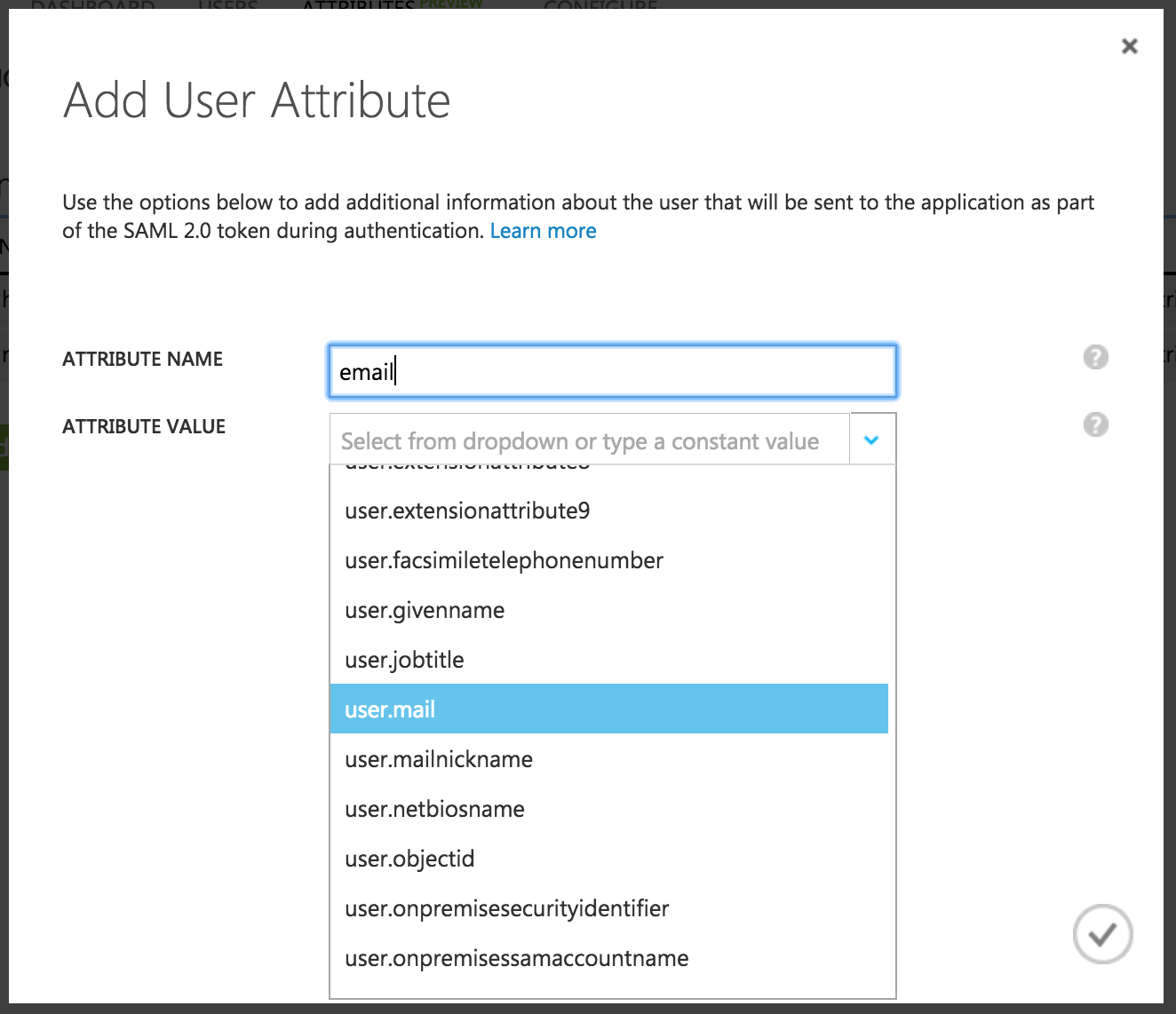
To add a row for
email,do the following:- Select add user attribute. The Add User Attribute modal displays.
-
Enter
emailin the ATTRIBUTE NAME field. -
Select “user.mail” in the ATTRIBUTE VALUE dropdown.
-
Select the checkmark at the bottom right of the modal.
Your final attributes should look like the screenshot below:

-
(Optional) If you want to add a title, phone, and/or group, do so now using the same workflow that you did for
nameandemail.
-
To add a row for
- Select Apply Changes. This concludes the SSO setup within Entra.
- In Domo, select Save Config.
Test Connection to Domo
Test your connection in Domo by clicking the Test Config button at the top of the Single Sign-On (SSO) page. Note: Entra may take up to five minutes to apply your settings, so the connection test may not immediately work. If you followed all the implementation steps correctly, you should see a success message. If not, review the above steps or contact Domo Support .
.