Intro
Domo supports single sign-on (SSO) using two protocols: Security Assertion Markup Language 2.0 (SAML) and OpenID Connect (OIDC). Both SAML and OIDC can operate concurrently. This article describes how to choose the best protocol—SAML or OIDC—for your use case and how to configure SSO with your chosen protocol. Depending on your configuration, SSO can also auto-provision Domo users and assign them their user role, attributes, and group membership.- Required grants
- Access SSO configuration settings
- SAML vs. OIDC: Choose a protocol
- Configure your IdP
- Configure SSO with SAML
- Configure SSO with OIDC
- Configure SSO settings
- Enable SSO and set defaults
- Set user role, attributes, and group membership
- Direct sign-on list
Required Grants
You must have the Admin system role or a custom role with the Manage All Company Settings grant enabled to set up SSO. Learn more about system and custom roles.Access SSO Configuration Settings
You can find Domo SSO configuration settings by navigating to Admin > Authentication > Single Sign-On (SSO).SAML vs. OIDC: Choose a Protocol
Domo supports both SAML and OIDC. Choosing which one to use depends on a few considerations. All other things being equal, OIDC is the more modern standard and a good choice. For Domo setup, management, and functionality, consider these differences:- OIDC may be easier to configure, especially if your IdP provides a well-known config.
- SAML requires certificate exchange and management, which introduces some overhead.
- Does your organization dictate which you should use?
- Is your team more familiar with one or the other?
Configure Your IdP
Refer to your IdP’s documentation for instructions on configuring the IdP side of SAML and OIDC SSO integrations. You may be asked for information from Domo. That information can be found in the SSO configuration user interface, and descriptions of that information for SAML and OIDC appear below.Configure SSO with SAML
After configuring your IdP, access the Domo SSO configuration settings as described above.-
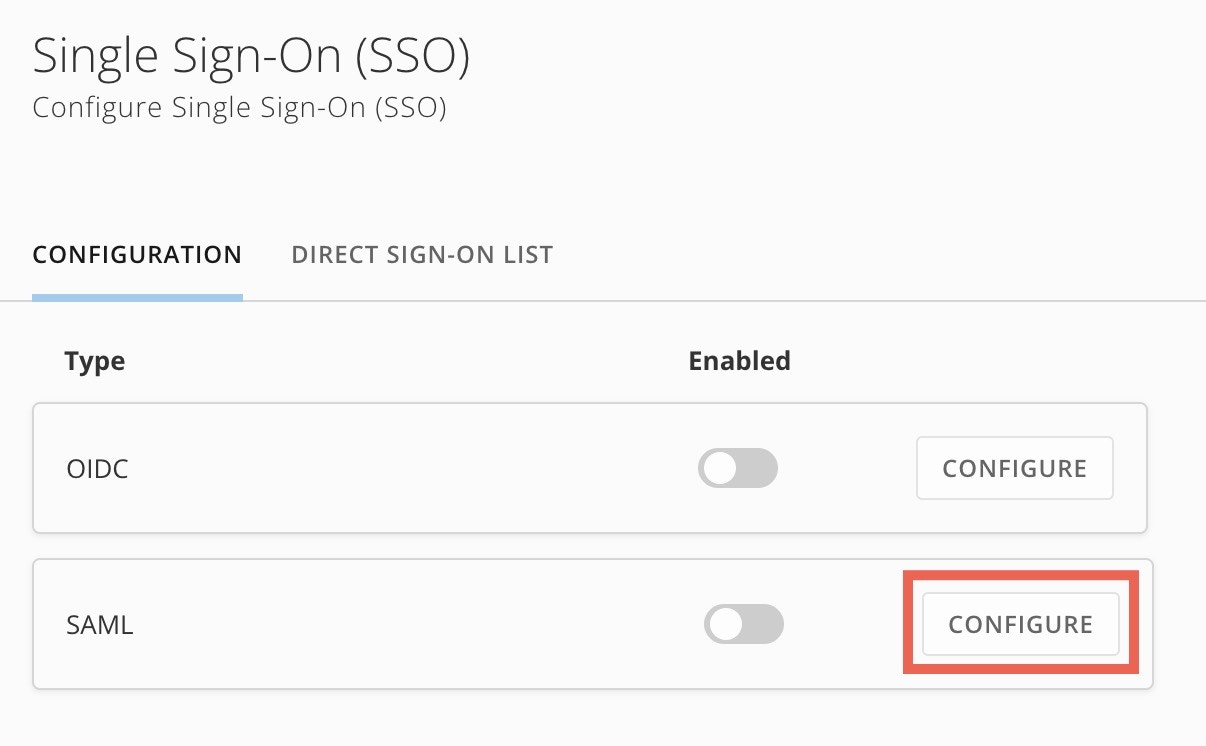
If SAML SSO hasn’t been configured previously, select Configure for the SAML item. You can then choose Upload Metadata or Manual Entry. Learn more about each option below.
-
If SAML was previously configured, you can edit the configuration by selecting
 More (three vertical dots icon) > Edit OR Upload metadata.
Note that uploading metadata will overwrite previously configured values.
More (three vertical dots icon) > Edit OR Upload metadata.
Note that uploading metadata will overwrite previously configured values.
Metadata Upload or Manual Entry
-
To upload metadata from your IdP, choose
 More (three vertical dots icon) > Upload Metadata in the configuration menu.
In the modal that appears, enter the metadata URL from your IdP and select Upload.
More (three vertical dots icon) > Upload Metadata in the configuration menu.
In the modal that appears, enter the metadata URL from your IdP and select Upload. The full SAML configuration screen displays. Uploading the metadata URL automatically sets configuration values in the Information from your IdP section and overwrites any values that may have been previously set.
The full SAML configuration screen displays. Uploading the metadata URL automatically sets configuration values in the Information from your IdP section and overwrites any values that may have been previously set.
- If your IdP doesn’t provide a metadata URL or if you don’t want to use it, choose Manual Entry in the configuration menu. With this option, you must manually enter the necessary information.
Information From Your IdP
As you configure your Domo SSO integration via SAML, you must provide some key pieces of information to define how Domo integrates with your IdP.Information Your IdP May Need
You may need to give the SAML app in your IdP some information about how it should integrate with Domo. This will depend on your IdP and how you’ve configured your SAML app. These values are defined in Domo, and your IdP may use different terminology. Each field is described below to help you understand the purpose of the information and how to identify the corresponding parameters to set in your IdP. For more details, refer to your IdP’s documentation.Field | Description |
|---|---|
| Domo Entity ID | The unique identifier of your Domo instance. This is sometimes known as the Issuer. |
| SAML assertion endpoint URL | The URL where your IdP will send SAML assertions after authenticating a user. This is also known as the Assertion Consumer Service (ACS) URL. |
| Domo x.509 certificate download | Your IdP can use this certificate to verify requests coming from Domo. If your SAML app is configured to verify authentication requests from Domo, you’ll need to upload this certificate to your SAML app in your IdP AND configure Domo to sign authentication requests. See Sign authentication requests below. |
| Metadata | Domo provides a metadata file that contains the above information, including Domo’s current x.509 signing certificate. You can download this metadata and upload it to your IdP—if metadata upload is supported—to simplify the configuration of your SAML app. |
Additional Settings
Configure the other SSO settings as necessary. These are discussed below.Save the Configuration
After entering the required information and configuring the settings, save the configuration. If SAML isn’t already enabled, you can choose to save and enable it or save without enabling it. Learn how to enable SSO below.Configure SSO with OIDC
After configuring your IdP, access the Domo SSO configuration settings as described above.-
If OIDC SSO hasn’t been configured previously, select Configure for the OIDC item.

-
If OIDC was previously configured, you can edit the configuration by selecting
 More (three vertical dots icon) > Edit.
More (three vertical dots icon) > Edit.
Information From Your IdP
As you configure your Domo SSO integration via OIDC, you must provide some key pieces of information to define how Domo integrates with your IdP. Most IdPs have a well-known config endpoint to make sharing this information easy, but if yours doesn’t, you’ll need to configure OIDC manually by providing the information that would otherwise be provided by the well-known config.Configure with Well-Known Config
-
After selecting Configure to open the configuration modal, select Well-Known Config if it isn’t already selected.

- Enter the following information associated with your Domo SSO app in your IdP. These values are defined in your IdP, which may use different terminology. Each field is described below to help you understand the purpose of the information and to help you find each value in your IdP, no matter what it’s called.
Configure Manually
If your IdP doesn’t provide a well-known config, you’ll need to manually enter the information that would otherwise be provided by the well-known config.-
After selecting Configure to open the configuration modal, select Manual Entry if it isn’t already selected.
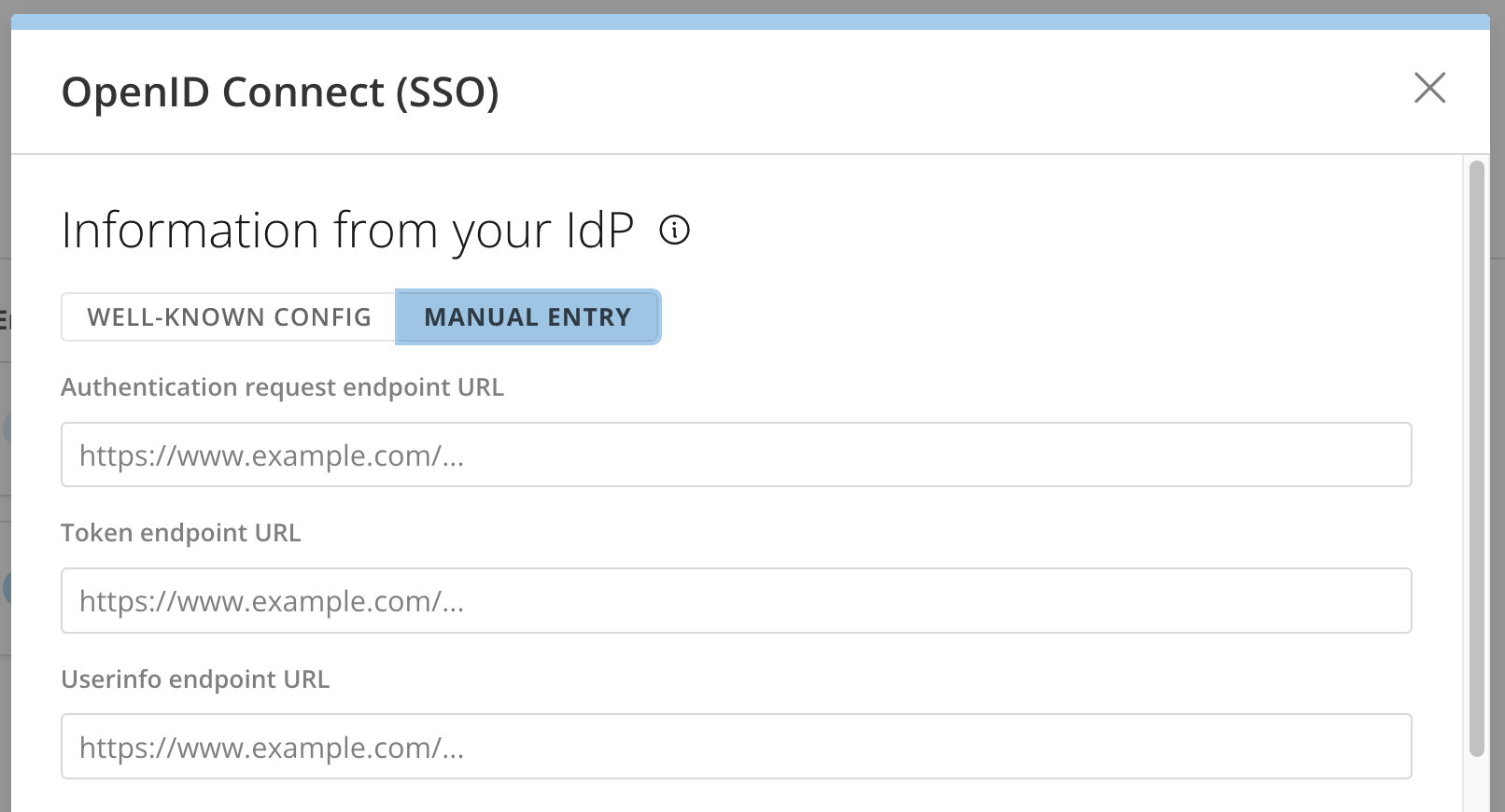
- Enter the following information associated with your Domo SSO app in your IdP. These values are defined in your IdP, which may use different terminology. Each field is described below to help you understand the purpose of the information and to help you find each value in your IdP, no matter what it’s called.
Information Your IdP May Need
Your IdP may need to know the OpenID Callback URL for your Domo environment. That URL is listed in the section of the configuration modal labeled Information your IdP may need. Open the modal from the SSO configuration settings by selecting Configure / More (three vertical dots icon) > Edit.
More (three vertical dots icon) > Edit.

Additional Settings
Configure the other SSO settings as necessary. These are discussed below.Save the Configuration
After entering the required information and configuring the settings, save the configuration. If OIDC isn’t already enabled, you can choose to save and enable it or save without enabling it.Configure SSO Settings
Field | Options | Description |
|---|---|---|
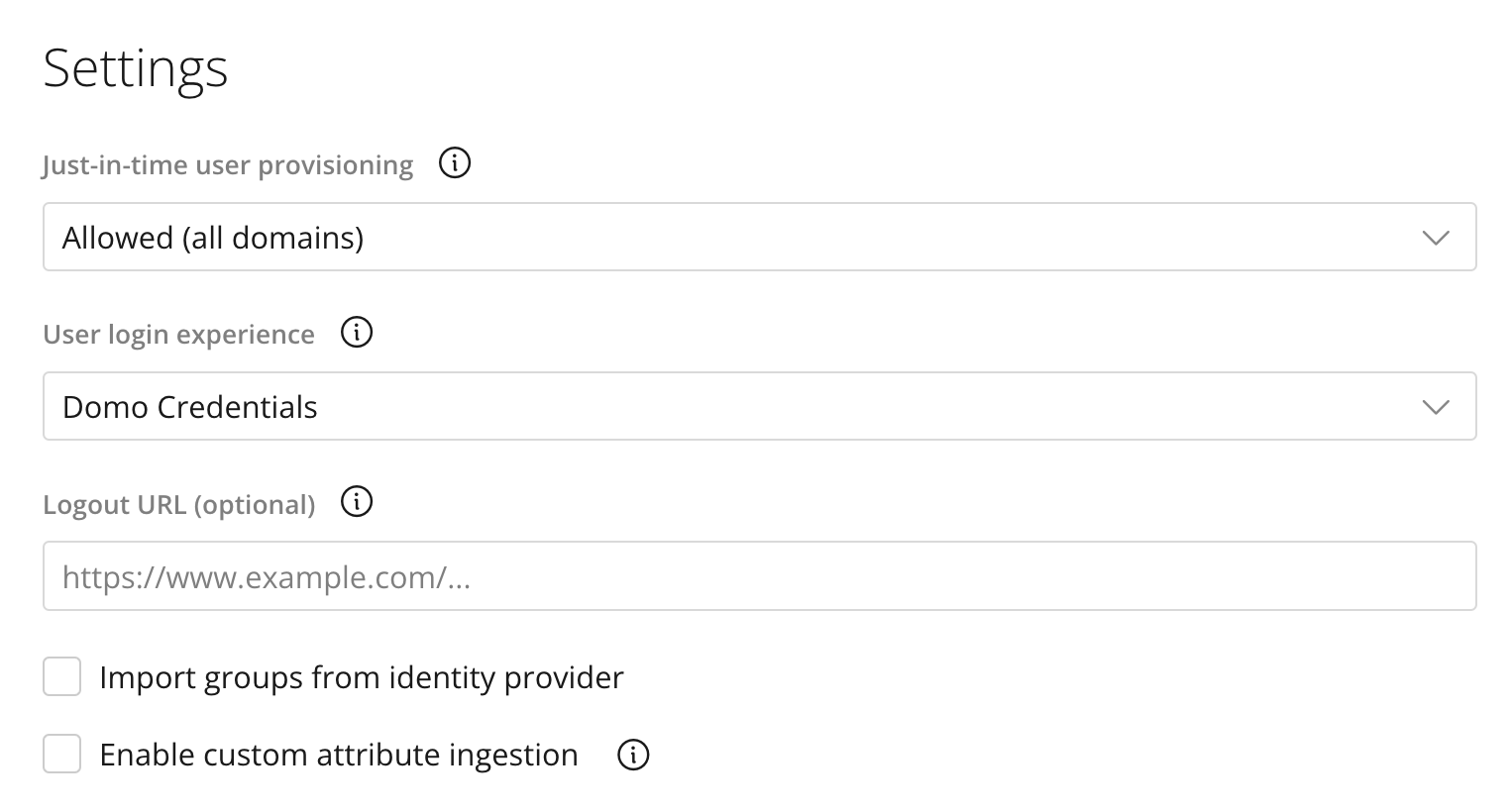
| Just-in-time user provisioning | Allowed (all domains) Allowed (authorized domains only) Disallowed | This setting governs the behavior when a user who does not exist in Domo attempts to log in via SSO. The behavior you choose should be influenced by your use case and the configuration of your IdP. For example, if your IdP is configured to allow any IdP user to log into Domo, you may want to disallow users from being automatically created in Domo. On the other hand, if you have a large and dynamic user base and your IdP controls user access to Domo, you may want to allow users to be automatically created in Domo. Learn how to specify authorized domains for invited users. |
| User login experience | Domo Credentials SSO (Domo auth screen) SSO (skip to IdP) | This setting governs the user’s experience when navigating directly to Domo. If all Domo users are expected to log in via SSO, you’ll likely want to configure this setting for SSO login (optionally presenting the Domo login screen or skipping the Domo login screen and immediately redirecting to your IdP).
|
| Logout URL (optional) | — | The URL users are redirected to when they log out of Domo. |
| Import groups from identity provider | — | This setting determines whether Domo directory groups will be created and their membership maintained by the SSO integration. If enabled, users are added to and/or removed from Domo directory groups as required when users log in via SSO. Learn about groups in Domo. |
| Enable custom attribute ingestion | — | If enabled, Domo will inherit values for custom Domo user attributes as users log in via SSO. Learn about setting attributes below. |
| (SAML only) Sign authentication requests | — | This setting governs whether Domo signs SAML authentication requests it sends to your IdP. If your SSO app in your IdP is configured to require authentication request signature verification, you’ll need to enable this AND load Domo’s x.509 signing certificate into your SSO app in your IdP. Domo’s certificate can be downloaded in the section of the SAML configuration modal labeled Information your IdP may need . |
| (SAML only) Use SAML relay state to redirect | — | If enabled, Domo will redirect users to the location (such as a specific Domo dashboard or app) specified in the SAML relay state. |
Enable SSO and Set Defaults
After you’ve configured SAML and/or OIDC, you must enable SSO using the switches in the SSO Configuration tab.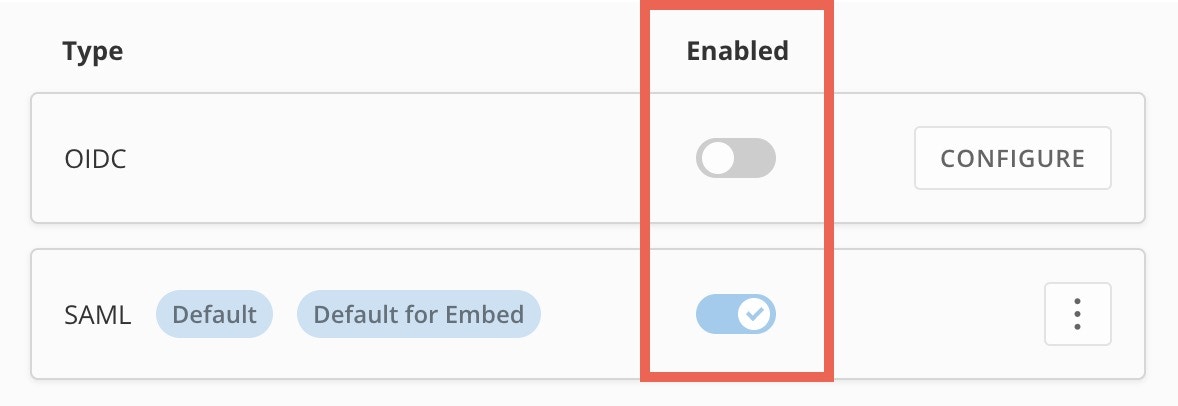
Set User Role, Attributes, and Group Membership
You can configure SSO to set/update user role, attributes, and group membership based on IdP-specified values as users log into Domo. User attributes in your IdP must be mapped to corresponding ones (identified by their key) in Domo. The following attributes are supported:Attribute | SAML assertion or OIDC claim | |
|---|---|---|
SAML | OIDC | |
Note: In Domo, the user’s unique identifier is their email address. The value included in the email attribute overrides the SAML Subject value in the SAML assertion. | ||
User Name Note: For SAML, if Note: For OIDC, several other claims are supported ( | name | name |
name.personal | Others. See note. | |
name.family | ||
Role Note: Domo supports only one role per user. The role value passed to Domo from the IdP must exactly match a role defined in Domo. If just-in-time provisioning is allowed, and if no acceptable role is provided by the IdP, the user will receive the default role for the Domo instance. Learn about managing roles and the default role . | role | Not supported |
| Secondary Email | email.secondary | alternate_email |
| Employee ID | employee. id | sub |
Employee Number Note: | employee. id | Not supported |
Hire Date Format: YYYY-MM-DD | hire.date | hiredate |
| Title | title | title |
| Department | department | department |
| Location | location | location |
| Mobile Phone | user.phone | phone_number |
| Desk Phone | desk.phone | desk_phone_number |
Locale Valid values: de-DE, de-AT, de-CH, en-AU, en-CA, en-150, en-HK, en-IE, en-IN, en-IL, en-MO, en-NL, en-NZ, en-SG, en-GB, en-US, en-001, es-ES, es-US, es-419, es-MX, fr-BE, fr-CA, fr-FR, fr-CH, nl-BE, nl-NL, pt-BR, pt-PT, ja-JP, zh-CN, zh-Hans-HK,zh-Hans-MO, zh-Hans-SG | locale | locale |
Time Zone Valid values: any TZ identifier as defined in the tz database | timezone | zoneinfo |
Any custom attribute defined in Domo. Note : Attributes must be defined in Domo before Domo will accept those attribute values from your IdP. See Attributes . | Key defined for the target attribute | Key defined for the target attribute |
Directory Groups Note: The directory group(s) the user is a member of. | groups | groups |
Direct Sign-on List
When enforced, the Direct Sign-on List designates the Domo users who can log into Domo directly with Domo credentials; other users must log in via SSO. The Direct Sign-on List is enforced if SAML is enabled and the SAML “User login experience” is set to “SSO (Domo auth screen)” or “SSO (skip to IdP)”.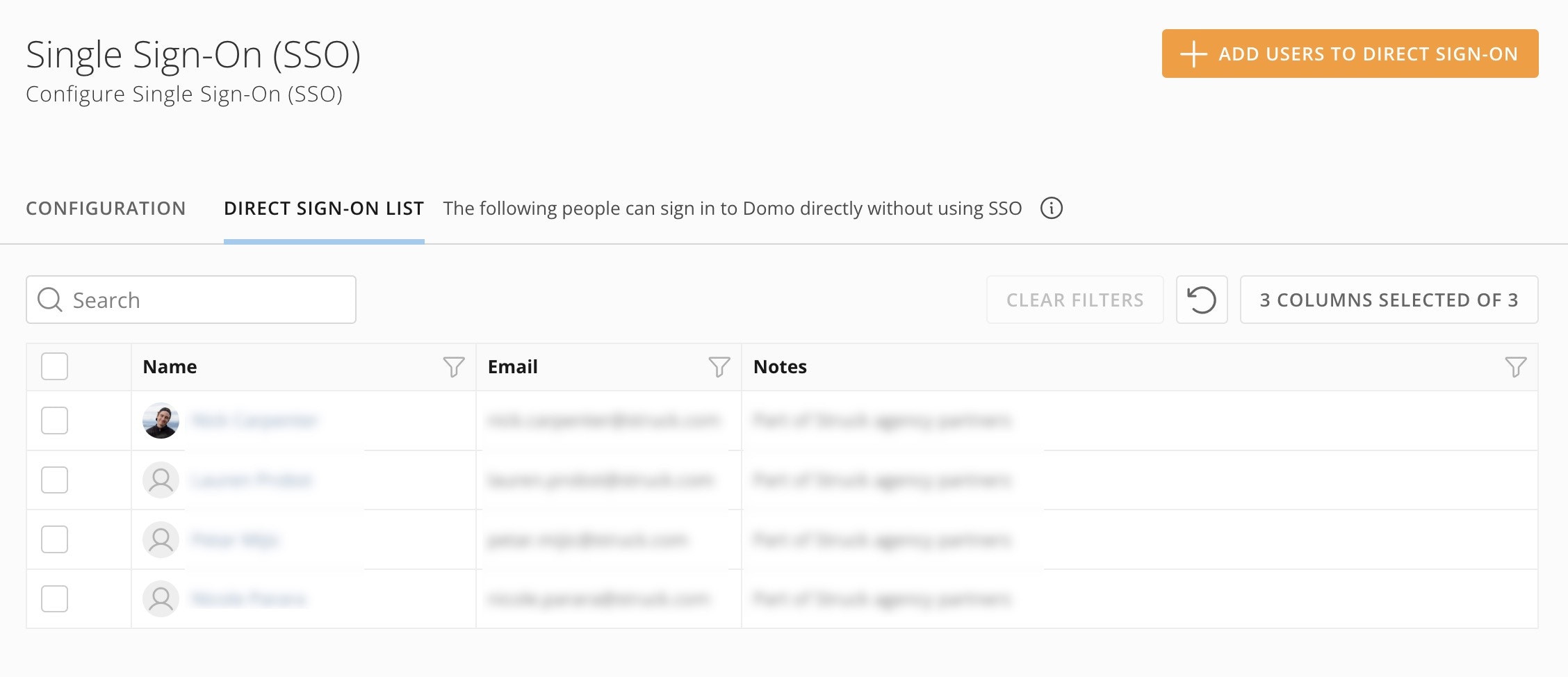
 More (three vertical dots icon) > Make default for sign in.
More (three vertical dots icon) > Make default for sign in. More (three vertical dots icon) > Make default for embed.
More (three vertical dots icon) > Make default for embed.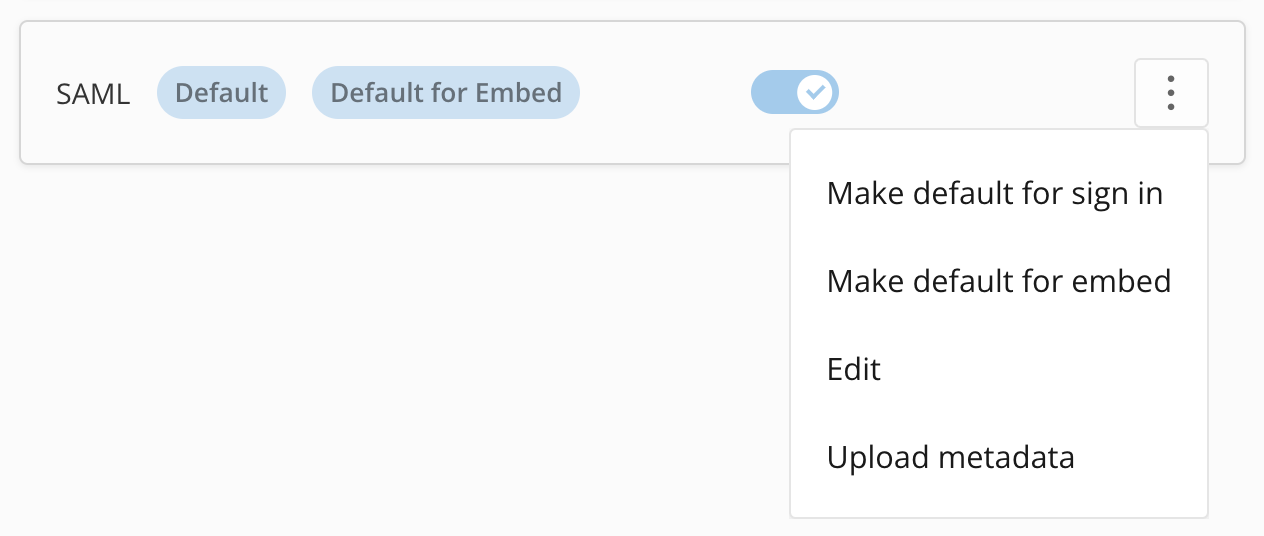
 .
.