Intro
Domo is an industry leader when it comes to mobile security. We have worked alongside global leaders in finance, health care, and other sensitive data industries to define, build, and deploy enterprise-ready security controls that safeguard your sensitive data while affording you all the benefits of the Domo platform. In addition to the benefits and security Domo offers out of the box, enterprise security features reduce dependencies on third-party security providers. These features give you the means to make sure your data is secure without degrading the Domo mobile experience.Session Control: Dynamic Timeout and Revocation
You can secure user access to your Domo instance and data with two controls:-
Absolute session timeout — This control allows you to set an absolute timeout duration which when reached requires all users to re-login.
- Example: The absolute session timeout is set to 21 days. Every 21 days each user must log in again.
-
Relative session timeout — This control allows you to set a relative timeout based on user activity. The timeout is in effect if the user has not used the application within the specified timeout duration.
- Example: The relative session timeout is seven days. If a user has not used the app for a continuous duration of seven days, then they must log in again. Any time they use the app, the seven-day count resets.
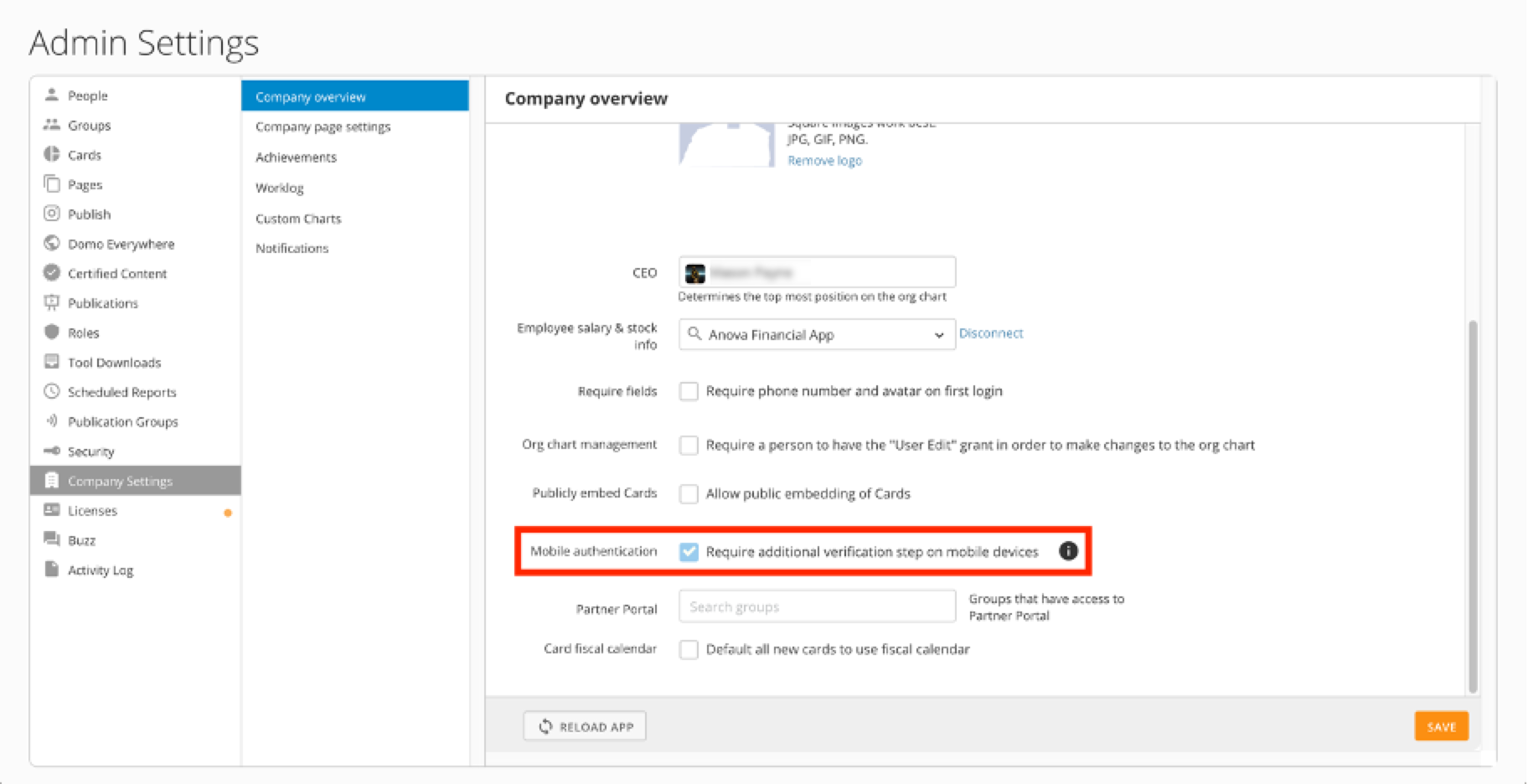
Native Device User Authentication
As an additional layer of security to add confidence that those accessing the device are the authorized users, Domo has added the additional layer of native device user authentication. Native device user authentication requires that any device running the Domo mobile app have an additional form of device security setup prior to and each time the user attempts to access the Domo mobile app. This is done in the form of biometric or passcode authentication depending on the technology of each device.
Enhanced Data Encryption
All push notifications sent to iOS devices are encrypted over https. Push notification payloads can be end-to-end encrypted on request. iOS and Android native encryption are used for any content which is cached on the device for increased performance. Cached content is wiped from the device with the termination of each user session. Domo encrypts all customer data that is stored in persistent storage within Domo. For this purpose, Domo utilizes Advanced Encryption Standard (AES) algorithm with a key size of 256 bits. To protect our customers’ data as it is transmitted across untrusted networks, Domo uses a combination of secure protocols, including TLS, with only a limited number of trusted ciphers supported. SSH and SFTP are also supported, where appropriate, for the secure transfer of data. Domo does not allow clear text or unencrypted data communication protocols. Domo best practice ensures that all Domo customers use at least one of the provided secured services (TLS, SSH, SFTP). We use TLS 1.2.