Intro
The System for Cross-domain Identity Management (SCIM) is a standard that defines API endpoints that systems can use to manage identity. With an SSO integration, Domo receives information about new or updated users only when they log into Domo. However, with SCIM, you can configure your identity provider (IdP) to create and/or update users and groups in Domo when those users and groups are created and modified in your IdP. .
.- Prerequisites
- Required grants & SCIM integration user
- IdP configuration
- Supported endpoints
- SCIM status
Prerequisites
Domo’s SCIM endpoints use header-based authorization with a Domo access token. Domo’s SCIM endpoints accept either of the two authorization headers, both of which require access tokens:- Authorization: Bearer < Domo Access Token >
- X-Domo-Developer-Token: < Domo Access Token >
Required Grants & SCIM Integration User
We recommend that you create a SCIM Integration custom role and user:- Create a “SCIM Integration Role” as a custom role in your Domo instance — This role can be assigned only the grants required to support your intended usage of the SCIM integration (see required grants below). Learn how to create and define custom roles.
- Create a “SCIM Integration User” in your Domo instance and assign it to the SCIM Integration Role — Domo’s SCIM endpoints require authorization using a Domo access token, and access tokens are associated with specific Domo users. Taking this approach, the access token used in the SCIM integration can be assigned to the SCIM Integration User.
- Manage All Users — This grant allows the holder to create, edit, and delete any user and reset their password.
- Manage All Roles — This grant allows the holder to create, edit, and delete custom roles and assign any role to any user.
-
Manage All Groups — This grant allows the holder to manage group settings, modify Ad Hoc Domo groups, and create and manage Directory groups via SCIM.
Note: This grant is not required if you don’t intend to use the SCIM Groups endpoints or the group-related attributes in the SCIM Users endpoint.
Note: These are all admin-level grants, included automatically with the Admin system role, and allow you to add and manage all aspects of users, including setting roles and changing passwords.
IdP Configuration
The SCIM integration between your IdP and Domo is configured on the IdP side. To get started, please refer to the documentation from your IdP. During configuration, you must configure which user attributes are synchronized to Domo from your IdP. Domo’s SCIM endpoints map elements from six SCIM schemas:User Endpoints
-
Core (urn:ietf:params:scim:schemas:core:2.0:User) -
Enterprise (urn:ietf:params:scim:schemas:extension:enterprise:2.0:User) -
Custom (urn:ietf:params:scim:schemas:extension:custom:2.0:User)
Group Endpoints
-
Domo (urn:ietf:params:scim:schemas:extension:domo:2.0:User) -
Group (urn:ietf:params:scim:schemas:core:2.0:Group) -
Domo Group (urn:ietf:params:scim:schemas:extension:domo:2.0:Group)
Domo Attribute & SCIM User Endpoints | SCIM Schema and Element |
|---|---|
User Name This is the user’s email address, which is the unique identifier for the user in Domo. | Core / userName |
Name | Core / displayName |
Core / emails / {emails (required), type [primary | alternate]} | |
Alternate email | Core / emails / {email (required), type [primary | alternate]} |
Role Domo supports a single role per user. | Core / roles / {id(required), name} |
Employee ID | Enterprise / employeeNumber |
Hire date | Domo / hireDate |
Title | Core / title |
Department | Enterprise / department |
Location | Domo / employeeLocation |
Mobile phone | Core / phoneNumbers / {phoneNumber, type [cell | desk]} |
Desk phone | Core / phoneNumbers / {phoneNumber, type [cell | desk]} |
Locale | Core / locale |
Timezone | Core / timezone |
Group | Core / groups / { value , display } Where value is the ID of the group in Domo and display is the group name as defined in the IdP. |
Organization | Enterprise / organization |
Manager | Enterprise / manager { value, display } Where value is the manager Domo user ID. |
All custom attributes Learn more about Domo custom attributes . | Custom / customAttributes [{ key , values }] Where key is the attribute key as defined in Domo and values are the user attribute values. |
Directory Name The group name as defined in the IdP. | Group / displayName |
Domo Group Display Name The group name in Domo that is most readily accessible to Domo users and is presented to users throughout the product, such as when sharing content or viewing card ownership. | Domo Group / domoDisplayName |
Description | |
Group Membership | Group / members / [{ value , display }] Where value is the Domo user ID of the group member and display is the username. |
Supported Endpoints
Domo’s SCIM implementation supports many standard endpoints. The endpoint information provided in the sections below is to help you configure your IdP. For details of what is required with each action, please refer to the SCIM spec .
Endpoint root:
.
Endpoint root:
Configuration and Schemas
The following configuration and schema endpoints are supported in Domo:Endpoint Name | Description | Endpoint |
|---|---|---|
Get Service Provider Configuration | Retrieves the SCIM features and functionality supported by Domo. | GET /ServiceProviderConfig |
Get Schemas | GET /Schemas | |
Get User Schemas | Retrieves the user schemas. | GET /Schemas/User |
User
The following user endpoints are supported in Domo:Endpoint Name | Description | Endpoint |
|---|---|---|
Get Users | Retrieves all users with different request parameters to filter users. The following request and filter parameters are supported:
| GET /Users |
Get User | Retrieves a user specified by their Domo userId. The requested attributes can be passed in as a comma-separated list via query parameters named “attributes.” Note that some attributes are always returned. | GET /Users/ Examples:
|
Put User | Updates a user by Domo userId. The user’s existing attributes will be completely replaced by the attributes specified in the PUT request. If you need to update partially existing users, use the PATCH user endpoint. | PUT /Users/ |
Patch User (Beta) | Partially updates a user’s attributes as specified in the request body. Most user attributes can be added, replaced, or removed. | |
Delete User | Deletes the specified Domo user. | DELETE /Users/ |
Post User | POST /Users |
Group (Beta)
Domo directory groups (groups defined in the IdP and created and managed in Domo via SSO or SCIM integration) can be created, managed, and deleted via SSO and SCIM. The SCIM APIs only function on directory groups. This means that groups created via SCIM are always directory groups, and the Get Group endpoint only returns information about directory groups. Learn more about directory groups and other group types in Domo. Domo’s SCIM integration functions in the context of the Domo user who owns the Domo Access Token used by the SCIM integration. (See our recommendations for the SCIM Integration User above.) To allow Domo directory groups to be managed via SCIM, the Domo SCIM Integration User must be designated in Groups Settings as the user permitted to manage directory groups. Follow these steps to designate the SCIM Integration User in Group Settings:- Go to Admin > Governance > Groups.
-
Select
 Group Settings (gear icon).
Group Settings (gear icon).
-
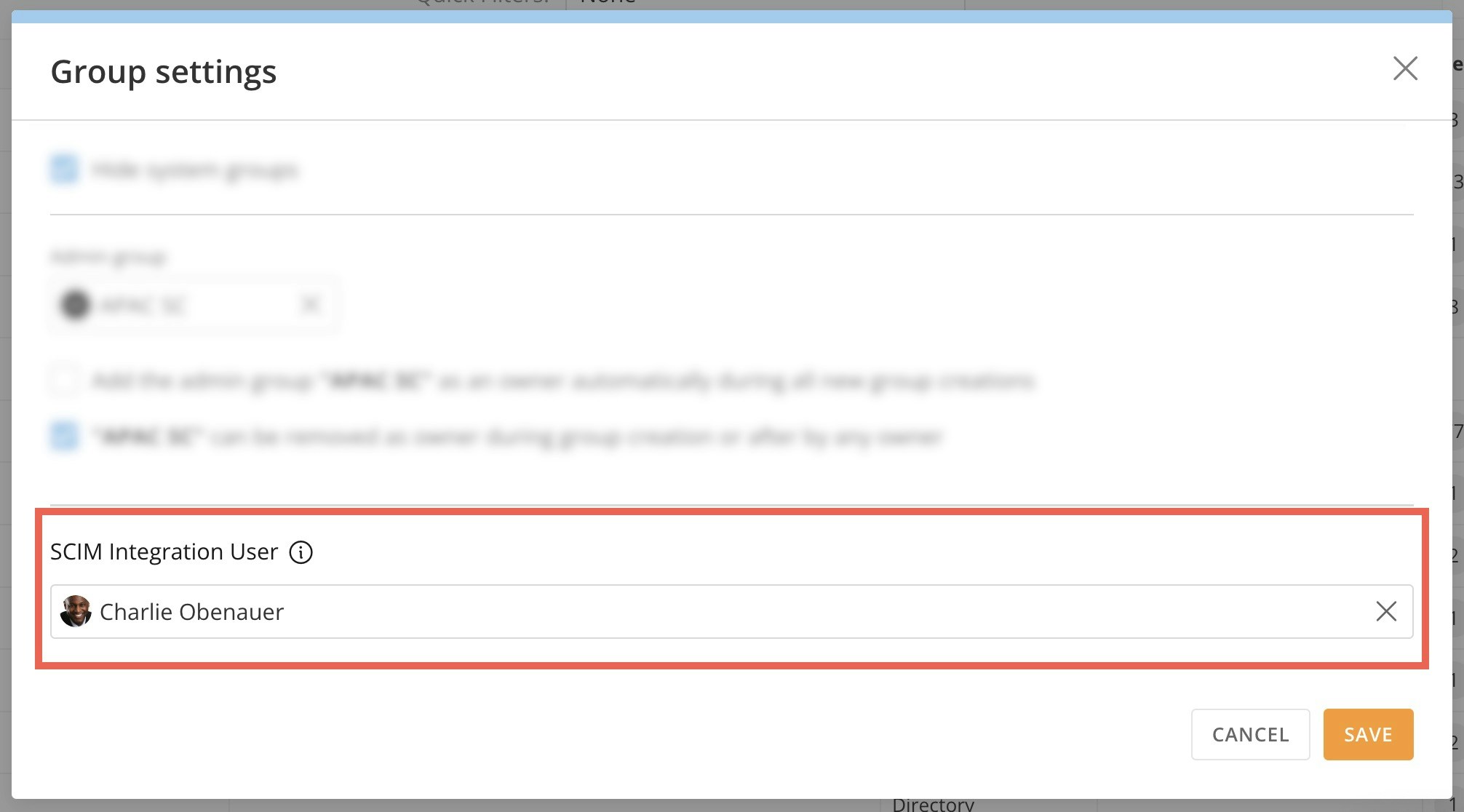
In the modal that displays, use the dropdown to choose the SCIM Integration User and save your changes.
SCIM Status
This table lists the status of each available action.| Type | Action | Spec-compliant APIs | Tested with Okta | Tested with Entra | Other |
| Config and Schema | GET Service Provider Configuration |  | |||
| Config and Schema | GET Schemas |  | |||
| Config and Schema | GET User Schemas |  | |||
| Users | GET Users |  | |||
| Users | GET User |  | |||
| Users | PUT User |  | |||
| Users | PATCH User | beta | |||
| Users | DELETE User |  | |||
| Users | POST User |  | |||
| Groups | GET Groups | beta | |||
| Groups | POST Groups | beta | |||
| Groups | PUT Groups | beta | |||
| Groups | PATCH Groups | beta | |||
| Groups | DELETE Groups | beta |