API Base URL
Security: Bearer AuthBasic authentication is a simple authentication scheme built into the HTTP protocol. To use it, send your HTTP requests with an Authorization header that contains the word Basic followed by a space and a base64-encoded string
username:password.Example: Authorization: Basic ZGVtbzpwQDU1dzByZA==OAuth Authentication
The following section provides more detail on the OAuth authentication and authorization approach. In order to access Domo APIs, a user must first be authenticated (prove that they are whom they say they are) through aclient ID and client secret.
Once a user has been authenticated, they can then create an access token to authorize what the scope of functionality will be available for each API for that specific access token.
Best Practice
The Domo SDKs (Java or Python) are often the recommended approach to leveraging the above Domo APIs: that’s because they provide a nice wrapper for each endpoint and automatically handle refreshing your access token. Learn more about our SDKs sdks.md.Security Consideration
A Client ID is a public identifier while the Client secret is considered confidential.Quickstart
To leverage the APIs in Domo will require you to obtain an access token. This quickstart will walk you through the three steps needed to authenticate and begin developing.
- Create client ID and secret
- Create access token
- Use access token
Step 1: Create client ID and secret
In order to generate a client ID and client secret you will need your Domo instance name (i.e. the name preceding your domo.com URL, in the case of “acmecompany.domo.com” your instance name would be acmecompany). To create a client ID and secret you will need to log in within the Developer Portal. You will be prompted to enter your instance name and then your user credentials.

Step 2: Create access token
Once you obtain your client ID and client secret you will then need to obtain your access token. You can do so in our interactive documentation using the Get Access Token endpoint or using the example
curl requst below.
scope,client_ID, and client_secret would look similar to below:
Best Practice
Domo’s SDKs simplify the authentication process. Obtain a Client ID and Client Secret and then update the placeholders to begin developing.Step 3: Use access token
Now that you have received your access token, you will use it for each of your request. It is recommended to simplify the process with the following request with:
Important terms
OAuth 2.0: OAuth 2.0 is an authentication framework as defined by the RFC-6749 standard. OAuth 2.0 focuses on client developer simplicity while providing specific authentication flows for web and desktop applications. Generally speaking, OAuth provides clients with secure delegated access to server resources on behalf of a resource owner. It allows resource owners to authenticate and authorize third-party access to their server resources without the need to share personal credentials. Designed specifically to work with Hypertext Transfer Protocol (HTTP), OAuth uses short-lived access tokens, issued to a client by an authentication server, with the approval of the resource owner. The client then uses the access token to access the protected resources hosted by the resource server. Client ID: An ID used to uniquely identify a third-party client. Client Secret: A secret code that proves to the authentication server that the client program is authorized to make a request on behalf of the user. Client Secrets are required for OAuth 2.0. A program requesting an access token has to know the client secret in order to gain the token. This prevents malicious apps that have not been authorized from ever obtaining a valid access token. A Client Secret doesn’t state anything about authenticating a user; it’s simply authorizing an app to request access tokens. A client secret must be protected at all costs; if the secret is compromised, a new one must be generated and all authorized programs must be updated with the new client secret.
OAuth 2.0 handshake summary
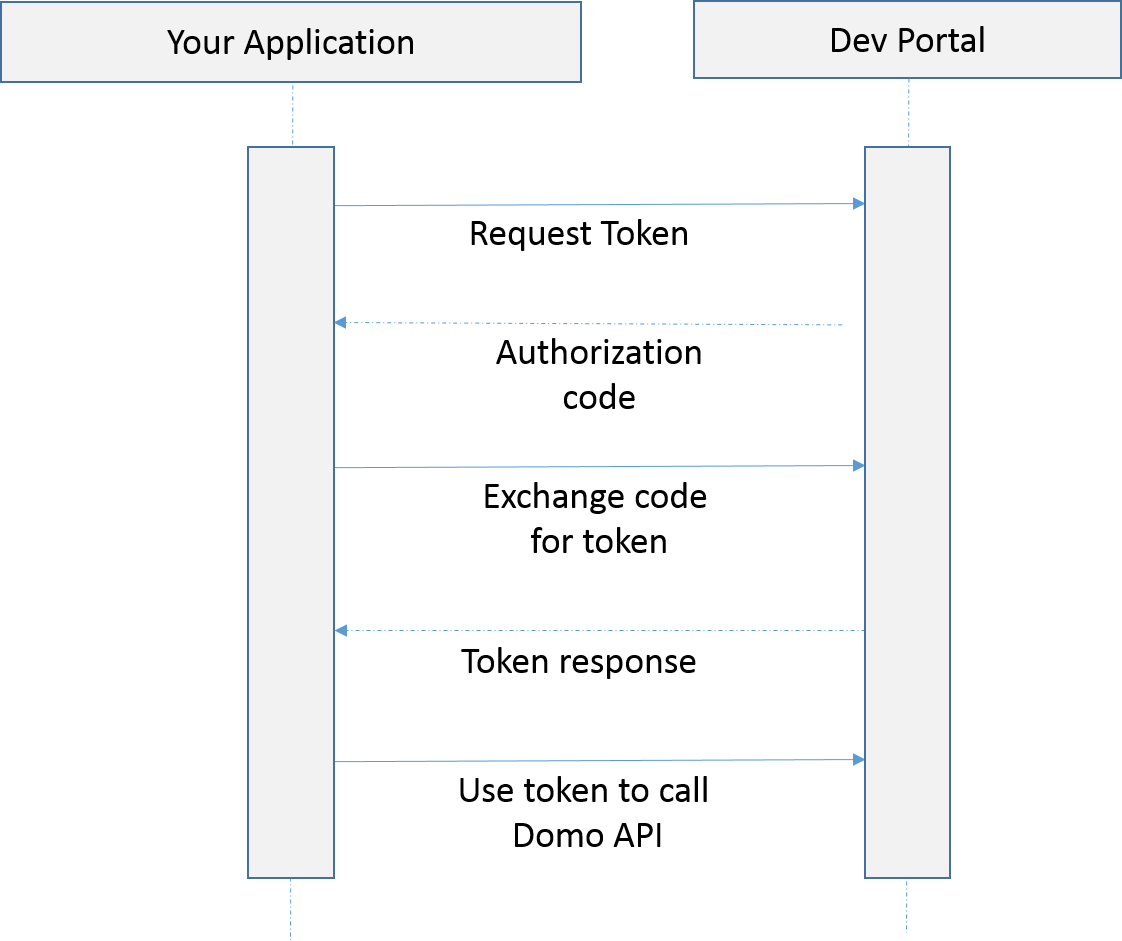
Next Steps
Start experimenting with the Domo OAuth APIs. In addition to the above approach from the command line, you can also generate an access token and test using directly within the Domo Developer Portal.
